Introduction
Technology has become an integral part of our lives and with the increased amount of media we use on a daily basis, managing the privacy of our data is very important. A robust and effective technique is needed to protect the privacy of important documents, such as medical records, banking records etc in order to mitigate the security threats and increase information security.
This method can be used to encrypt and hide sensitive data and information such as medical records.
Objective
Transferring digital information and data over the internet is a concern to security and privacy as the data is more susceptible to illegal copying. So in order to protect the ownership and copyright claims we aim to improve the data privacy, security as well as ownership of multimedia applications and files such as images using techniques of Cryptography and Steganography.
Concepts Involved
The project explores the following concepts:
Cryptography:
Cryptography is the technique of achieving security by encoding messages to make them impossible to understand. It provides solutions to many problems like data encryption, authentication, key distribution etc.
Cryptography provides a medium of secure communication that allows only the sender and intended recipient of a message to view and process the contents. Thus preventing unauthorized access to the information.
The algorithms involve the use of mathematical concepts and set of rules in order to encode the messages and are used for key generation, digital signing that enables them to be widely used in various applications such as the browsers, chat applications such as WhatsApp, as well as internet calling applications such as Google Duo
Hill Cipher
Hill Cipher is a polygraphic substitution cipher based on the concepts of linear algebra. It makes use of modulo arithmetic, matrix inverses and matrix multiplications.
In Hill Cipher encryption and decryption, each letter is represented by a number mod 26
For encryption, a block of N letters is multiplied by an NxN invertible matrix, that is the key for encrypting the message.
For decryption, matrix multiplying the inverse of the key matrix with the ciphertext produces the decrypted plaintext.
ECC
Elliptic curve cryptography (ECC) is a key-based technique for encrypting data. It focuses on pairs of public and private keys for decryption and encryption of web traffic.
It uses elliptic curves in order to generate security between key pairs for public key encryption.
ECC can be described as an alternative technique to RSA, but it has an edge over RSA as it offers keys of smaller size and as it is based on elliptic curves structure, the keys are more difficult to crack mathematically which enables less computing power and stronger resistance to various attacks.
Steganography
Steganography hides the messages inside a cover that can be an image or video in such a way that its presence is undetectable. The cover is an ordinary, non-secret, file or message used in order to avoid detection. The secret data is then extracted at its destination.
Steganography can be used to conceal almost any type of digital content, including text, image, video or audio content and the data to be hidden can be hidden inside almost any other type of digital content.
The use of steganography can also be combined with encryption as an extra step for hiding or protecting data in order to increase the difficulty of detecting the secret content.
DCT
Discrete Cosine Transform is a transformation method that decomposes an image into parts of deferring importance. DCT is used a lot in compression tasks as well.
DCT is similar to Fourier-related transforms but it only uses real numbers.
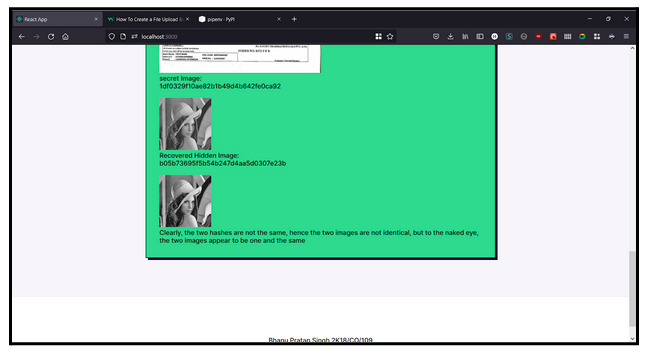
Since images can be compressed using the DCT, the algorithm has been used to transform the secret image into a smaller sized image, which can be embedded into the base (cover) image.
40% of the coefficients of the DCT are being used. This compresses the secret image in a lossy compression manner and the recovered image cannot be expected to be identical to the original image, however, as we can see in the implementation, it does a pretty good job of compression and the 2 images are very much similar to each other.
A mathematical expression is applied to all the pixels of the image, represented as a matrix to produce a new matrix of the same dimensions to get the DCT of an image.
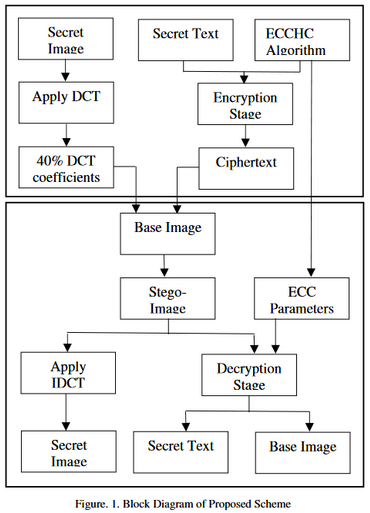
Implementation
Algorithm based on ECC and Hill Cipher has been used
Ciphertext as well as the DCT of an image are embedded into a base image, based on LSB watermarking
ECC generates a key
Based on this key, the ciphertext is generated using Hill Cipher.
Hard to extract the hidden image without the proper key.
Embedding Algorithm
Cryptography and steganography are used in this steps:
Cryptography step:
- Key for encryption is generated by a key generation algorithm using ECC.
- This key is then used in the Hill Cipher algorithm to encrypt the plaintext message.
- DCT is applied to the secret image, 40% of these DCT coefficients are embedded into the base image
Steganography steps:
- Least Set Bit technique is used to embed encrypted data into the base image.
Extraction:
- The secret key is needed to decrypt the message from the stego image.
- The secret image can be reconstructed using DCT coefficients.
Advantages of Method
-
Combining two techniques in order provides enhanced data security, ownership, and privacy.
-
The usage of ECC reduces the overall computation overhead.
-
Combining ECC with the Hill cipher algorithm increases the security and robustness against the attacks.
Applications
This project has a very important application in the field of healthcare
The medical history of any individual is very sensitive and private to that individual
It is important to make sure that the medical record of an individual is kept safe and secure
Now-a-days, all of us are using technology to digitally record everything we have, and we may do so for our medical records as well, however, in case there is a breach and the medical records reach the wrong hands, loss can be incurred
This project enables one way of safely digitising medical records for archival purposes.
The name and other details which can be used to identify a person can be redacted from the medical prescription or a medical record.
The medical record can then be used as a base image.
The details of the individual to which the medical record belongs can then be encrypted and embedded into the medical record itself, which does not contain any identity related information in itself.
This new medical record along with the key can then later be used to retrieve the details of the individual along with the medical record.
A secret image, such as XRay or CT Scan, and so on can in turn, also be hidden inside the base image; and can also be retrieved later.
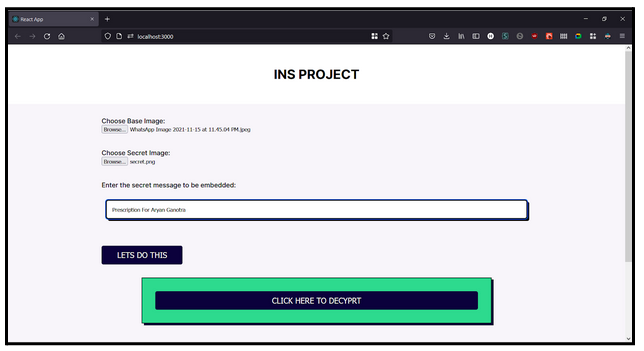
Choosing a base image, a secret image and the Hidden Message
On hitting submit, we get as response the stegano image
Here, we can see the MD5 Hash of Base Image and the Stegano Image.
Clearly, the two hashes are different which proves that the Stegano Image is different from the Base Image. The same applies for the recovered image and the secret image
On hitting submit, we get as response the stegano image
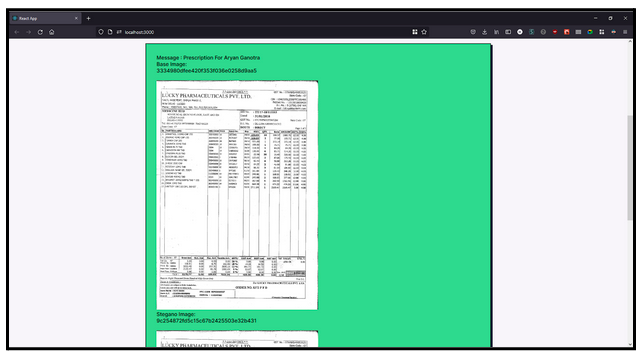
Here, we can see the MD5 Hash of Base Image and the Stegano Image.
Clearly, the two hashes are different which proves that the Stegano Image is different from the Base Image. The same applies for the recovered image and the secret image


















![Pepcoding : A platform to learn coding [it’s FREE!!] pepcoding-logo](https://codingee.com/wp-content/uploads/2021/05/logo-218x150.png)